The Domain Name Service (DNS) entries for all servers must be properly configured for Mediasite to operate successfully. The fully qualified domain name (FQDN) of the web and media servers should be used when configuring the Mediasite Video Platform software. These FQDNs are used in the Mediasite application to specify the location of slide images and video playlists to viewers. When using Mediasite in a network that implements NAT to map internal private IP addresses to publicly accessible addresses, the DNS names of the servers used by Mediasite should resolve to the appropriate public or private IP address.
Example

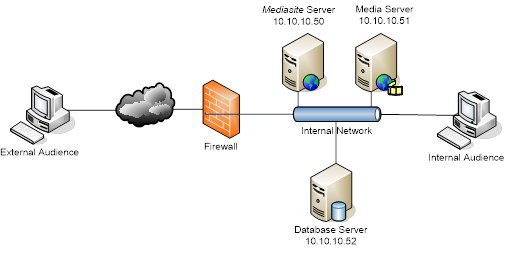
Network with a firewall between the servers and the public internet
The Mediasite Video Platform server is assigned the private IP address 10.10.10.50, the media server is assigned 10.10.10.51, and the database server is assigned 10.10.10.52. A firewall between the servers and the public Internet maps 10.10.10.50 and 10.10.10.51 to the public addresses 128.1.1.60 and 128.1.1.61, respectively. The DNS names chosen for the servers are mediasiteweb.example.com and mediasitevideo.example.com. Mediasite communicates with the database server on the internal network, so the database server does not need a public address.
The external viewer should resolve the names mediasiteweb.example.com to 128.1.1.60 and mediasitevideo.example.com to 128.1.1.61. However, a viewer on the internal network should resolve the names to 10.10.0.50 and 10.10.0.51, respectively.
The DNS administrator of the domain in question should be contacted to properly register the DNS entries on the internal and external DNS servers for the Mediasite Video Platform server and the media server.
In most networks using NAT, this setup will require a DNS server on the internal network. If an internal DNS server does not exist, connection attempts from internal viewers to the public IP addresses of the Mediasite Video Platform server and the media server should be tested. Often, this type of traffic is not permitted due to anti-spoofing rules on firewalls.